WWW.404MEDIA.CO
This Company Turns Dashcams into Virtual CCTV Cameras. Then Hackers Got In
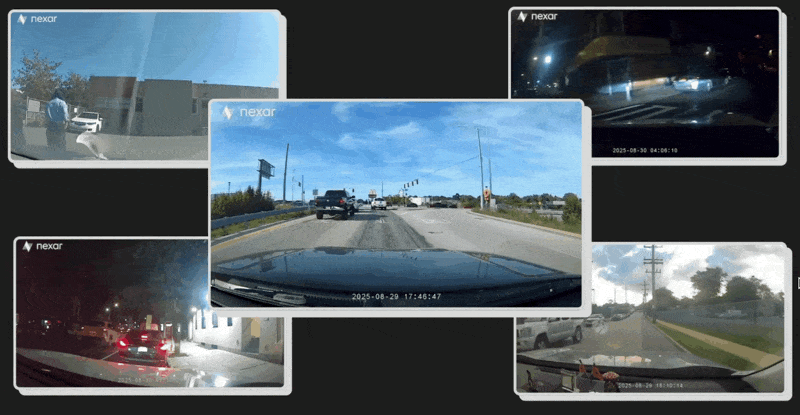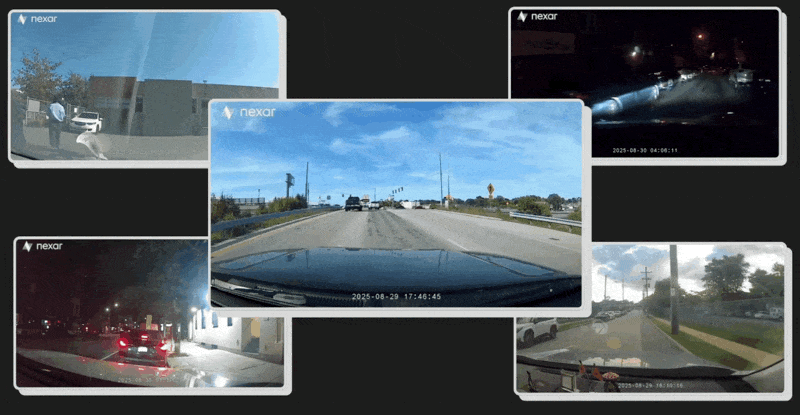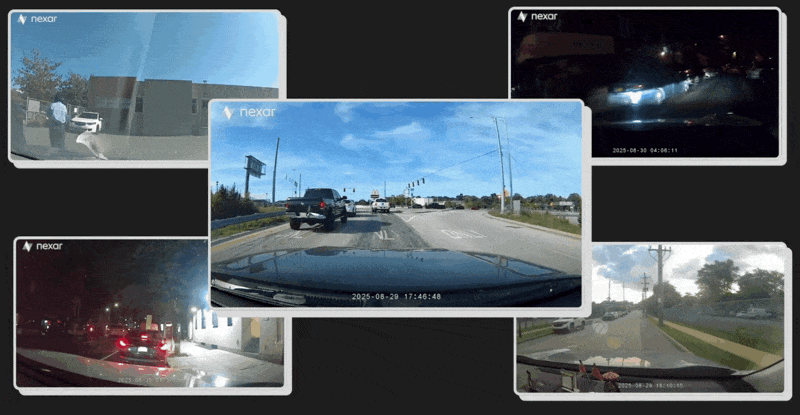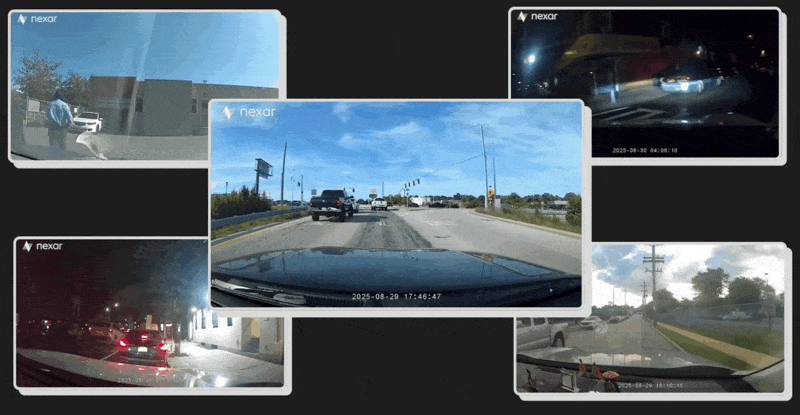
A hacker has broken into Nexar, a popular dashcam company that pitches its users dashcams as virtual CCTV cameras around the world that other people can buy images from, and accessed a database of terabytes of video recordings taken from cameras in drivers cars. The videos obtained by the hacker and shared with 404 Media capture people clearly unaware that a third party may be watching or listening in. A parent in a car soothing a baby. A man whistling along to the radio. Another person on a Facetime call. One appears to show a driver heading towards the entrance of the CIAs headquarters. Other images, which are publicly available in a map that Nexar publishes online, show drivers around sensitive Department of Defense locations.The hacker also found a list of companies and agencies that may have interacted with Nexars data business, which sells access to blurred images captured by the cameras and other related data. This can include monitoring the same location captured by Nexars cameras over time, and lets clients explore the physical world and gain insights like never before, and use its virtual CCTV cameras to monitor specific points of interest, according to Nexars website.The breach shows in stark terms the security and privacy risks of adding an always-on camera to vehicles, be that the risk to individuals, or even governments that dont want data related to their facilities or employees accessed by hackers or potentially other governments. It also shows that companies around the world have at least explored leveraging dashcam-related data for their own purposes, including Microsoft, Apple, and Google, a host of AI companies, and even Pokmon Go creator Niantic, according to the document that lists organizations that Nexar says have had access to its data.Nexar is an absolute privacy nightmare, their security is embarrassing, I would be very surprised if no one (foreign government or just bad actor) wasnt already tapping their customer data, the hacker behind the breach told 404 Media. I was able to in 2 hours or so. Do you know anything else about Nexar or any other company mentioned here? I would love to hear from you. Using a non-work device, you can message me securely on Signal at joseph.404 or send me an email at joseph@404media.co.The hacker provided a few dozen or so Nexar dashcam recordings for verification purposes.In one clip, the Nexar camera is faced inwards to the car, capturing what appears to be a rideshare driver picking up passengers. Like in many other videos, the peoples faces are clearly visible.Many, of course, show vehicles driving down a road or highway.As well as letting users record their own trips, Nexar monetizes users data and recordings by repackaging them into various products. One of those is the companys CityStream map, which displays recent and blurred images taken by Nexar dashcams on a publicly available map and annotates things such as yield or speed limit signs, damaged roads, and other hazards. The idea is for companies or public bodies to then pay for access to more of this data. Three Nexar users 404 Media spoke to all said they did not know that Nexar was posting user dashcam images publicly like this. The images on this site have license plates, faces, and car dashes blurred. Bruno Fernandez-Ruiz, Nexar co-founder and CTO, told 404 Media in an email that per Nexars privacy policy, users contributing to CityStream are either opt-out or opt-in depending on the jurisdiction.The hacker highlighted that some of these images were taken inside vehicles that appeared to be entering sensitive U.S. government facilities, such as the Whiteman Air Force Base, Missouri, which houses B-2 stealth bombers, and Offutt Air Force Base, Nebraska, which is the headquarters of U.S. Strategic Command. One showed a Nexar user driving on the road towards 1000 Colonial Farm Road, the CIAs headquarters.From there, the hacker was able to find an unblurred video from this specific CIA-related user in the terabytes of hacked data. It showed the driver taking an exit off a road that heads towards the headquarters. The end of the clip shows them removing the camera from the dashboard itself.The CIA did not respond to a request for comment on its policies concerning staff or visitors use of personal dashcams, such as are they required to remove them from the dashboard before approaching headquarters or other facilities. Multiple representatives of the Air Force did not respond to requests for comment.The hacker said they were able to access one of Nexars AWS buckets, a type of database run by Amazon Web Services, in which they found more than 130 terabytes of data. That included raw recordings from peoples dashcams and GPS data, the hacker said. The issue, the hacker said, was that embedded in every Nexar dashcam was a key to this database which had too high privileges, allowing anyone with the key not just to upload their own cameras data, but also access that of everyone else. Nexar fixed this issue after being contacted by 404 Media this week. Fernandez-Ruiz said these recordings were users private backups.A screenshot from an image on Nexar's public map showing a car entering Whiteman Air Force Base.The hacker also broke into Nexars Atlassian instance, a company that makes collaboration tools such as Jira and Trello, and obtained a file laying out companies and organizations that Nexar says have had access to the company's data. Beyond its CityStream product, Nexar also offers Virtual Cam, which gives access to anonymized images captured by the dashcams over time. In a demonstration video, Nexar shows a user selecting a location in New York City, being shown the most recently captured dashcam image, then using a timeline to scroll backwards and see earlier images from the same location.One organization with access to Virtual Cam data is listed as IDF, according to the document. It says this organization has access to data inside Israel. Fernandez-Ruiz said We do not work with the Israeli Defense Forces. The Israel Defense Forces did not respond to a request for comment. Nexar is headquartered in Tel Aviv and New York.Entities that have had access to Nexar data include big tech companies like Apple, Microsoft, Amazon, and Google; Pokmon Go creator Niantic; transportation companies Lyft and Waymo; the cities of Los Angeles and Austin; and many AI and logistics focused companies, according to the document.Microsoft said that it explored using Nexar imagery for mapmaking purposes before March 2023, but that the work did not proceed beyond that evaluation stage. Google said it couldnt comment on relationships with specific companies, but that it uses third party imagery to update its maps. Amazon said it evaluated Nexar data to improve driver safety a few years ago and decided not to work with the company. Apple said it did not enter a partnership with Nexar. Lyft and Waymo did not respond. Niantic declined to comment.Last week 404 Media reported that surveillance company Flock, which has directly and indirectly provided data to Customs and Border Protection (CBP) and Immigration and Customs Enforcement (ICE), is looking to integrate with Nexar. Flock is included in the list of companies and organizations given access to Nexar data. In the product column it says Flock has All, and under location it says Worldwide. A Flock spokesperson told 404 Media Flock and Nexar do not currently have an integration, and we have no products available for customers. Fernandez-Ruiz said Flock Safetys access to CityStream as part of our collective partnership evaluation is definitively restricted to blurred, unidentifiable data.Researchers who have used Nexars blurred data have previously raised privacy concerns with it. In a paper published in June, they wrote Despite good-faith efforts by DSI [dense street imagery] providers to protect individual privacy through blurring faces and license plates, these measures fail to address broader privacy concerns. In this work, we find that increased data density and advancements in artificial intelligence enable harmful group membership inferences from supposedly anonymized data. They point to examples such as a high viz vest still revealing that a blurred person works for the NYPD.The NYPD is also listed in the hacked internal material as having had access to Nexars Virtual Cam product. An agency spokesperson said The NYPD does not have a formal relationship or contract with Nexar and we have not purchased any data from them. The spokesperson did not reply when asked if the NYPD had any sort of informal relationship with Nexar, or whether it evaluated the companys data.Nexars global customer base and their access to CityStream for road intelligence are all subject to strict privacy guidelines and protocols that prevent access to personally identifiable information, Fernandez-Ruiz added.Update: this piece has been updated to include a response from Apple.
0 Commentaires
0 Parts
38 Vue
0 Aperçu